Exporting Symantec Cloud SWG Logs to Splunk via Docker
This guide walks through the entire process of deploying Splunk in Docker, installing the Symantec Cloud SWG App and Add-on, configuring API access, and successfully ingesting Cloud SWG logs.
1. Prerequisites
- A Linux host (Ubuntu 20.04/22.04 or similar)
- Docker and Docker Compose installed
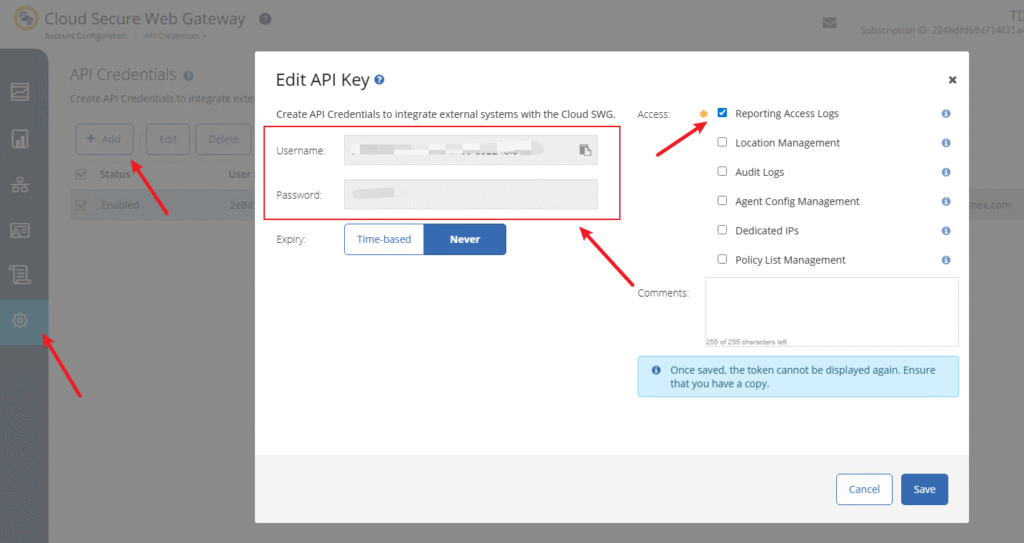
- Access to the Symantec Cloud SWG portal (portal.threatpulse.com)
- A valid API User and API Key
2. Install Docker
Run the following commands on Ubuntu:
# Install dependencies
sudo apt-get update
sudo apt-get install -y ca-certificates curl gnupg
# Add Docker’s official GPG key
sudo install -m 0755 -d /etc/apt/keyrings
sudo curl -fsSL https://download.docker.com/linux/ubuntu/gpg -o /etc/apt/keyrings/docker.asc
sudo chmod a+r /etc/apt/keyrings/docker.asc
# Add repository
echo \
"deb [arch=$(dpkg --print-architecture) signed-by=/etc/apt/keyrings/docker.asc] https://download.docker.com/linux/ubuntu \
$(. /etc/os-release && echo "${UBUNTU_CODENAME:-$VERSION_CODENAME}") stable" | \
sudo tee /etc/apt/sources.list.d/docker.list > /dev/null
# Install Docker Engine
sudo apt-get update
sudo apt-get install -y docker-ce docker-ce-cli containerd.io docker-buildx-plugin docker-compose-plugin
Verify:
docker --version
3. Deploy Splunk with Docker
Bind-mount directories for persistence:
mkdir -p /srv/splunk/etc /srv/splunk/var docker run -d --name splunk \ -p 8000:8000 \ -p 8089:8089 \ -p 9997:9997 \ -p 1514:1514 -p 1514:1514/udp \ -p 8088:8088 \ -e SPLUNK_GENERAL_TERMS=--accept-sgt-current-at-splunk-com \ -e SPLUNK_START_ARGS=--accept-license \ -e SPLUNK_PASSWORD='YourAdminPassword!' \ -v /srv/splunk/etc:/opt/splunk/etc \ -v /srv/splunk/var:/opt/splunk/var \ splunk/splunk:9.0.5
- Splunk Web:
https://<host-ip>:8000 - Admin username:
admin - Password: as set above
4. Install the Symantec Cloud SWG Add-on and App
- Download the TA-SymantecWebSecurityService (Add-on) and SymantecWebSecurityService (App).
- Download from: Symantec WSS App for Splunk
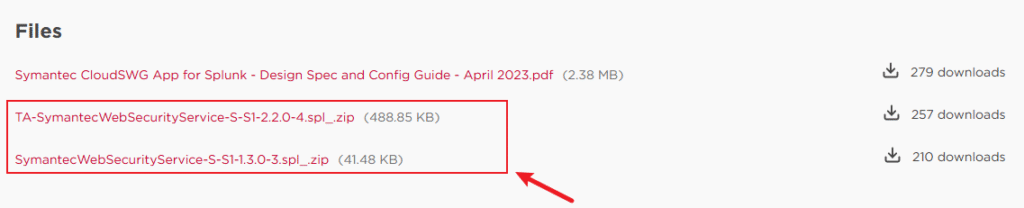
- In Splunk Web:
- Go to Apps > Manage Apps > Install app from file
- Upload both
.splpackages - Restart Splunk
5. Configure Cloud SWG Data Input
- In Splunk Web: Settings > Data Inputs > Symantec Web Security Service Rest Input Modular
- Create a new input with:
| Parameter | Value |
|---|---|
| Name | CloudSWGLogs |
| Portal URL | portal.threatpulse.com |
| API User Name | Cloud SWG API User Name |
| API Key | Paste your API key (twice) |
| Interval | 300 (for testing purpose) |
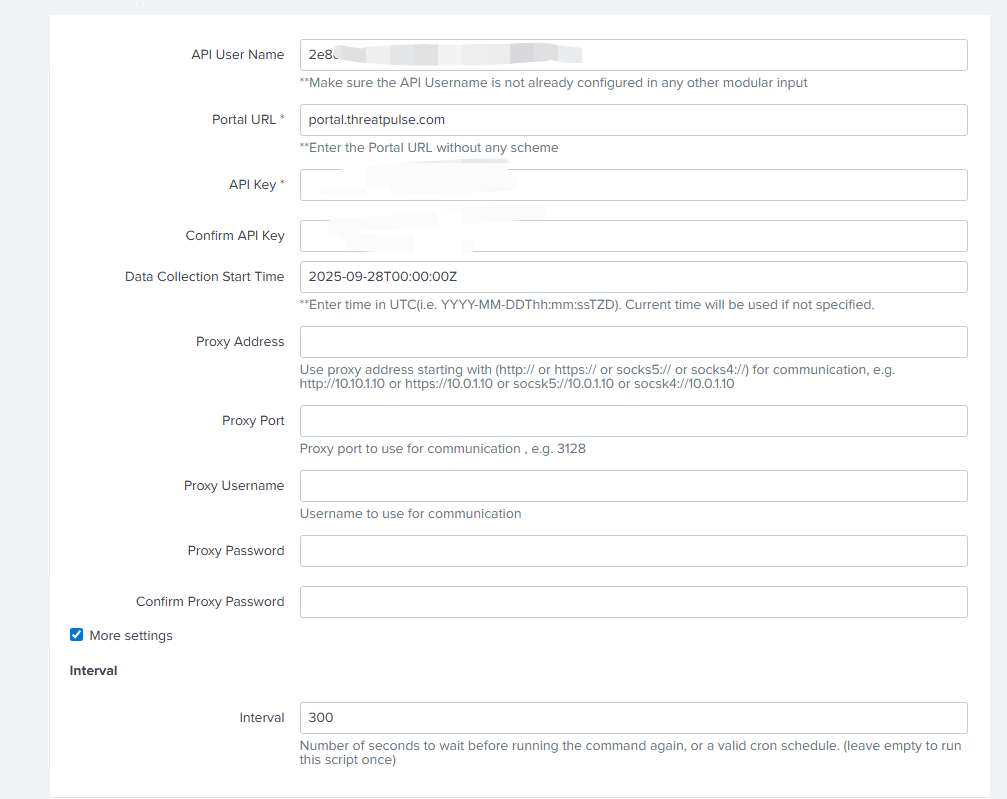
- Save and restart Splunk.
6. Troubleshooting the “Invalid cross-device link” Error
By default, the Add-on downloads logs to:
/opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/
and moves them to:
/opt/splunk/var/spool/splunk/
In Docker, these directories often reside on different volumes, so os.rename() fails with:
root@HF-Ubuntu-02:~# docker exec -it splunk bash
[ansible@97657274e7e9 splunk]$ sudo -i
[root@19889267ec34 bin]# cd /opt/splunk/var/log/scwss/
[root@19889267ec34 scwss]#
[root@19889267ec34 scwss]# cat scwss-poll.log
2025-09-30 01:25:49,091 INFO 128290507106112 - Script starting invocation at 2025-09-30 01:25:49
2025-09-30 01:25:49,210 INFO 128290507106112 - SWSS: Starting data collection...
2025-09-30 01:25:49,210 INFO 128290507106112 - Invoking API Request at 2025-09-30 01:25:49
2025-09-30 01:25:53,977 INFO 128290507106112 - Response received with status code 200
2025-09-30 01:25:54,803 INFO 128290507106112 - File name is cloud_archive_250930012550_stash_ta_scwss_logs.zip, size is 35.6494140625 kilobytes
2025-09-30 01:25:54,803 INFO 128290507106112 - File cloud_archive_250930012550_stash_ta_scwss_logs.zip downloaded from the API in 5 seconds
2025-09-30 01:25:54,804 ERROR 128290507106112 - SWSS: Error while writing data into Splunk: [Errno 18] Invalid cross-device link: '/opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/cloud_archive_250930012550_stash_ta_scwss_logs.zip' -> '/opt/splunk/var/spool/splunk/cloud_archive_250930012550_stash_ta_scwss_logs.zip'
Traceback (most recent call last):
File "/opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/scwss-poll.py", line 745, in run_script
os.rename(download_file, destination_path)
OSError: [Errno 18] Invalid cross-device link: '/opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/cloud_archive_250930012550_stash_ta_scwss_logs.zip' -> '/opt/splunk/var/spool/splunk/cloud_archive_250930012550_stash_ta_scwss_logs.zip'
Solution: Patch the Add-on Script
Edit /opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/scwss-poll.py:
[root@19889267ec34 scwss]# cd /opt/splunk/etc/apps/TA-SymantecWebSecurityService/bin/
[root@19889267ec34 bin]# vi scwss-poll.py
token = x_sync_token.decode()
# Edit Here!
# os.rename(download_file, destination_path)
import shutil
shutil.move(download_file, destination_path)
file_to_disk_end_time = time.time()
This replaces the default os.rename(...) with shutil.move(...), which transparently handles cross-filesystem moves.
Restart Splunk after editing:
docker restart splunk
Logs should now ingest successfully.
7. Verify Data
Search in Splunk:
index=main sourcetype="symantec:websecurityservice:scwss-poll" | head 20
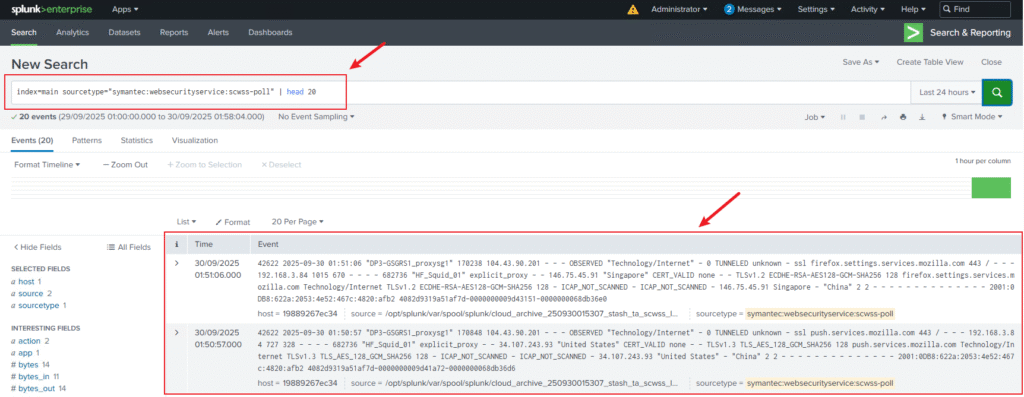
If results appear, dashboards such as Security Overview, Web Threat View, and Client View will populate.
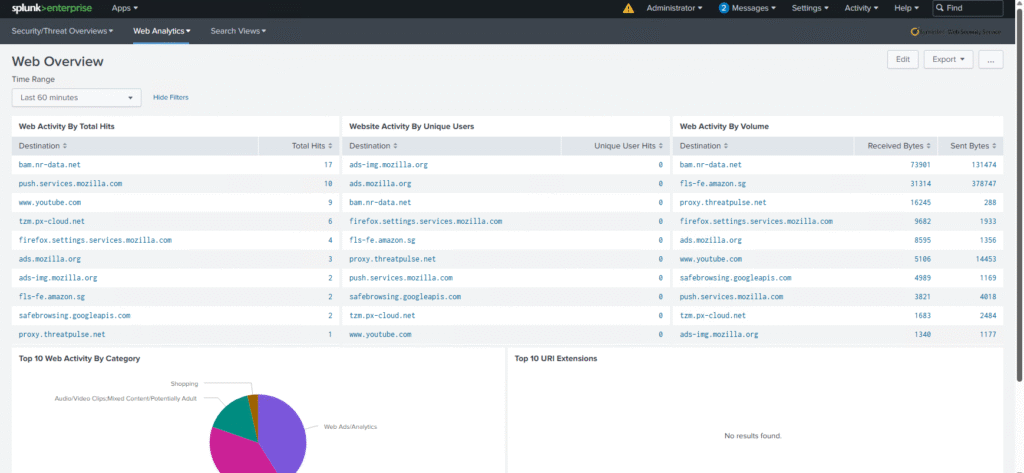
With this setup, you now have a working integration of Symantec Cloud SWG → Splunk, running entirely inside Docker.
Recent Comments