Integrating Symantec Cloud SWG with SEP/SES
This guide describes how to integrate Symantec Cloud SWG (formerly WSS) with Symantec Endpoint Protection (SEP) or Symantec Endpoint Security (SES) clients using a Provisioning Token and SAML authentication.
The integration ensures that all endpoint web traffic is redirected through Cloud SWG, with seamless user identification and consistent policy enforcement.
1. Prerequisites & Network Access
- Client versions: SEP/SES 14.3 RU5 or later (required for Using WSS SAML Authentication mode).
- Identity Provider (IdP): SAML-capable IdP such as Azure Entra ID, Okta, or SimpleSAMLphp, already integrated with Cloud SWG.
If endpoints connect through a corporate firewall or proxy, the following destinations and ports must be allowed without restrictions:
| URL | Port(s) | Purpose |
|---|---|---|
proxy.threatpulse.net | 8080 | Default Cloud SWG proxy endpoint |
sep-wtr.threatpulse.net | 8080 | SEP/SES Web and Cloud Access Protection (WTR) proxy endpoint |
client-id.wss.symantec.com/sso | 443 | Seamless identification (client ID exchange and token negotiation) |
2. Configure Cloud SWG
The detailed SAML configuration depends on your chosen IdP (Azure Entra ID, Okta, SimpleSAMLphp, etc.).
You can reference these step-by-step guides for Cloud SWG + IdP integration:
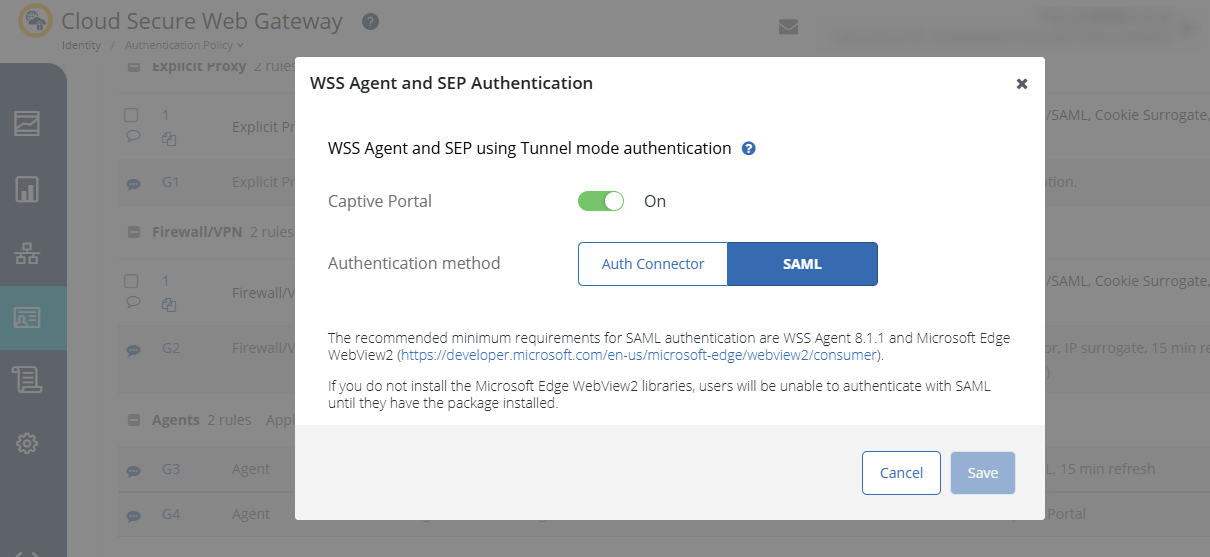
- Enable WSS Agent and SEP Authentication – SAML Captive Portal in the Cloud SWG Portal – Authentication Policy.
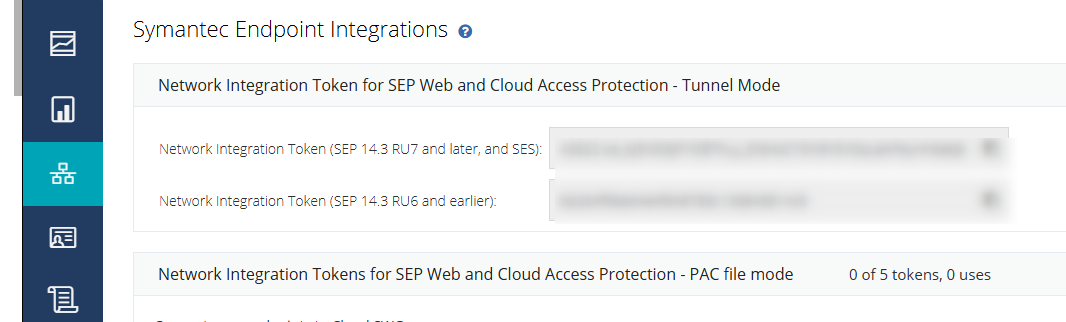
- Go to Connectivity → Symantec Endpoint Integrations, copy Network Integration Token(Tunnel Mode).
3. Configure SEPM
If you manage endpoints with SEPM:
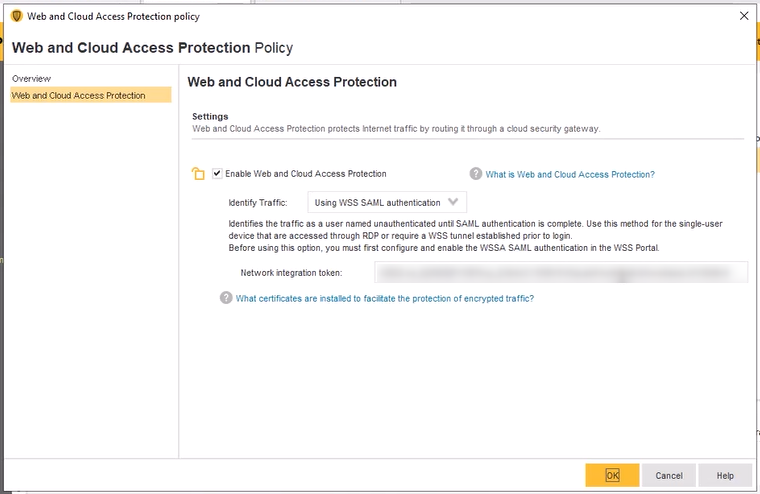
- In SEPM console: go to Policies → Web and Cloud Access Protection.
- Enable Web and Cloud Access Protection.
- Under Network integration token, paste the Token obtained from Cloud SWG.
- Select Identity traffic option: Using WSS SAML Authentication.
- Assign the policy to the appropriate client group.
- Trigger a policy update on the client (right-click → Update Policy) or wait for heartbeat.
4. Configure SES Cloud Console
If you manage endpoints with SES (cloud console):
- Navigate to the correct Domain.
- Go to Policies → Create Policy → Web and Cloud Access Protection.
- Enable the policy, paste the Network Integration Token, and choose Using WSS SAML Authentication.
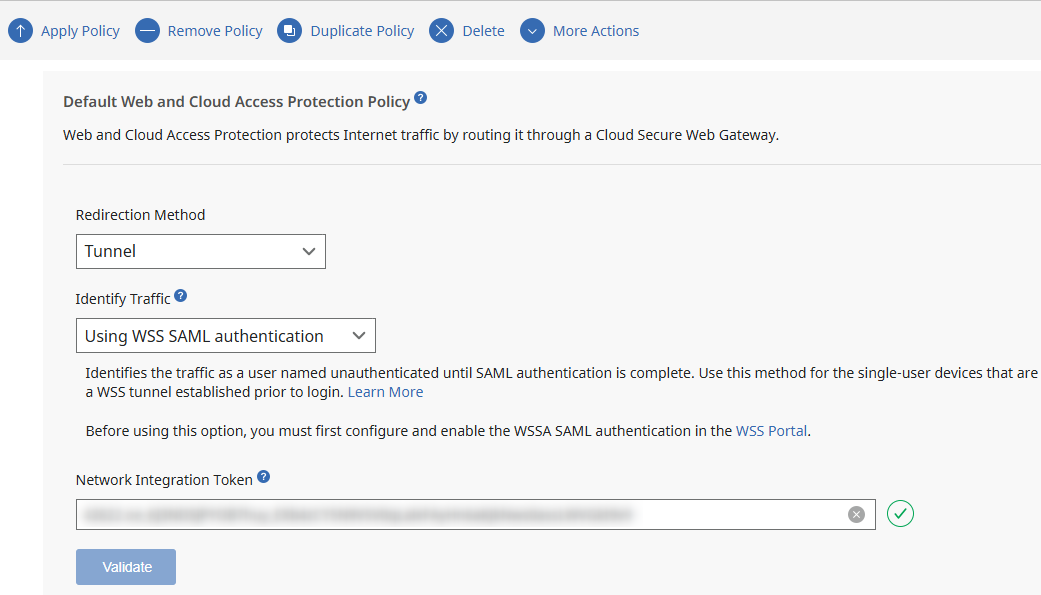
- Assign the policy to the desired Device Groups.
5. Endpoint Behavior and Verification
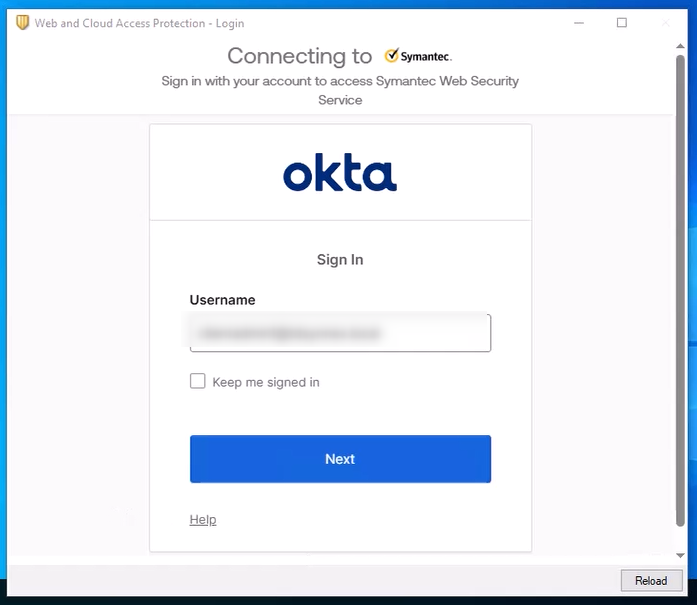
Once the policy is applied, the SEP/SES client will attempt to establish a secure tunnel to Cloud SWG.
On first-time use, the client will trigger a SAML login flow.
The user will be redirected to the IdP login page to complete authentication.
Recent Comments