Configuring GitHub Securelet in Symantec CloudSOC
This guide describes how to configure the GitHub Securelet in Symantec CloudSOC, connect it with a GitHub organization account, and test the setup by creating a sample activity (such as an Issue) to trigger a policy violation notification.
1. Prerequisites
- A CloudSOC administrator account
- A GitHub Organization with an Owner account
- At least one repository in the GitHub organization
2. Enable and Configure the GitHub Securelet
- Log in to the CloudSOC console.
- Navigate to Securelets → GitHub – Accounts and click Add New Account.
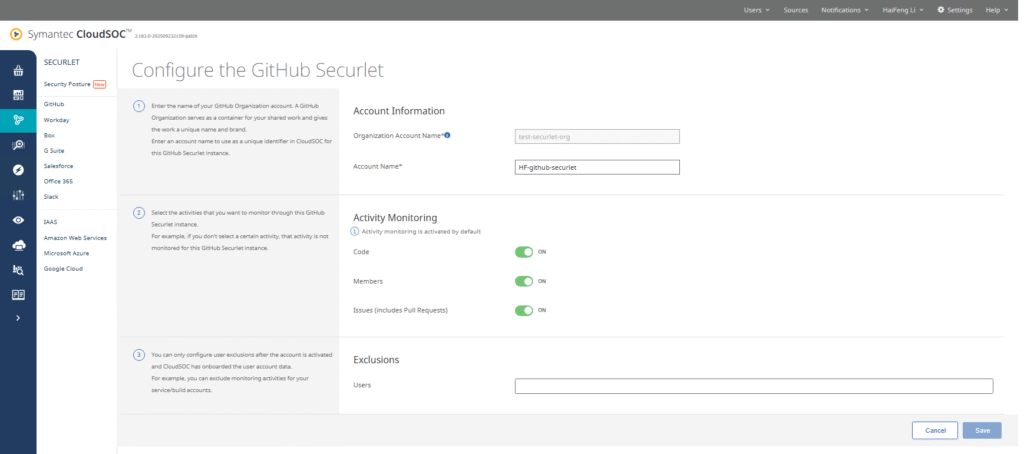
- On the Securelet configuration screen:
- Enter the Organization Account Name (e.g.,
test-securet-org) - Provide an Account Name (e.g.,
HF-github-securelet) - Enable monitoring for:
- Code
- Members
- Issues (includes Pull Requests)
- Enter the Organization Account Name (e.g.,
- Activate the configuration.
- You will be redirected to GitHub.
- Log in with your GitHub Organization Owner account.
- Approve the requested permissions
The Securelet is now active and monitoring activities.
3. Create a Policy for Activity Monitoring
- Go to Protect → Policies → Add Policy.
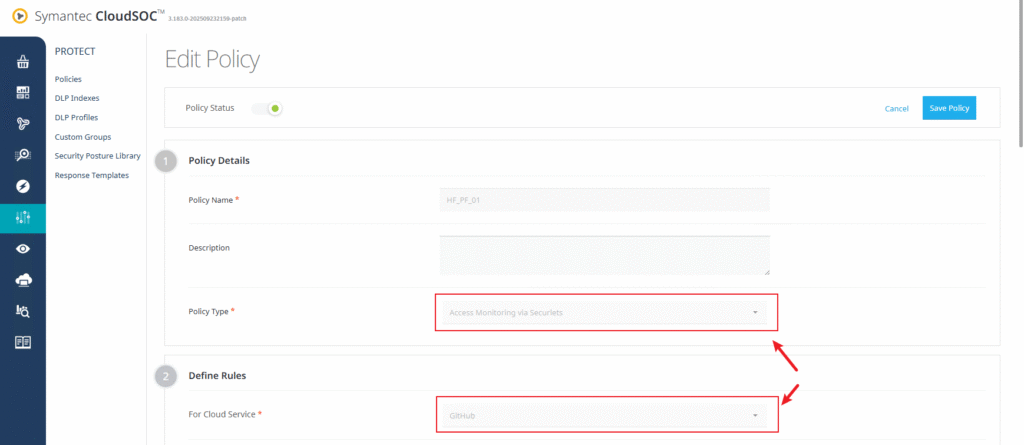
- Provide policy details:
- Policy Name: e.g.,
HF_PF_01 - Policy Type: Access Monitoring via Securelets
- Cloud Service: GitHub
- Policy Name: e.g.,
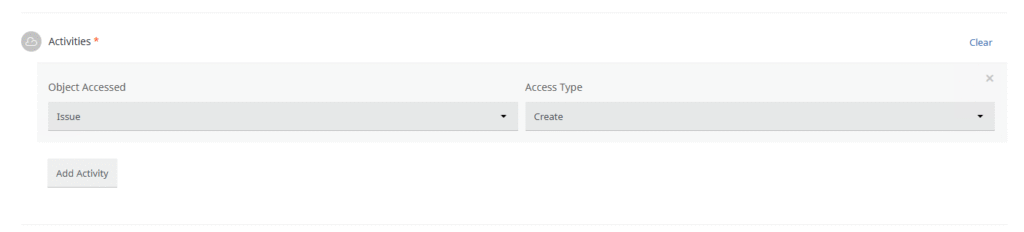
- Define the rule to monitor the desired activity. For example:
- Object Accessed: Issue
- Access Type: Create
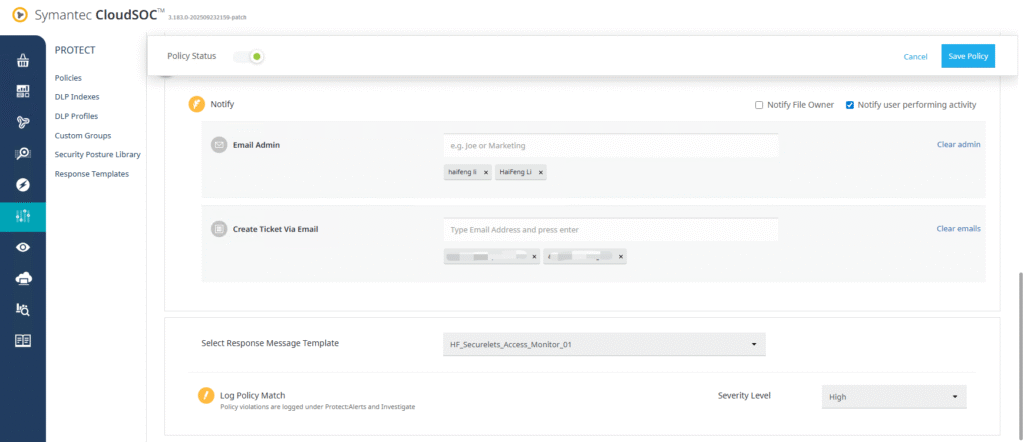
- Configure enforcement actions:
- Notify Admin via Email
- Notify User Performing Activity
- Assign a Response Message Template and set the severity level (e.g., High).
- Save and enable the policy.
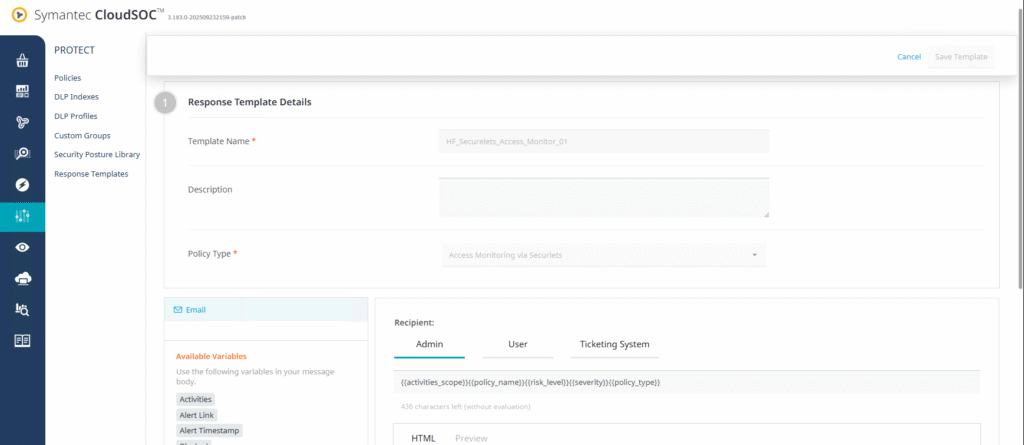
4. Configure a Response Template
- Go to Protect → Response Templates → Add Template.
- Enter template details:
- Template Name: e.g.,
HF_Securelets_Access_Monitor_01 - Policy Type: Access Monitoring via Securelets
- Template Name: e.g.,
- Define the message body using available variables such as:
{{activities_scope}}{{policy_name}}{{risk_level}}{{severity}}{{policy_type}}
- Specify recipients for notifications:
- Admin
- User
- Ticketing System
This ensures alerts can be automatically sent to admins, end users, and external ticketing systems. Don’t forget to reference this Response Template in the Policy configuration so that it will be applied correctly.
5. Perform a Test Activity
To validate the Securelet setup:
- Open a repository in your GitHub Organization.
- Perform the monitored action (e.g., create an Issue):
- Title:
CloudSOC Securelet Test - Description:
This Issue was created to validate the GitHub Securelet policy.
- Title:
- In the CloudSOC console, go to Securlet → GitHub → Activities.
- You should see the recorded GitHub event.
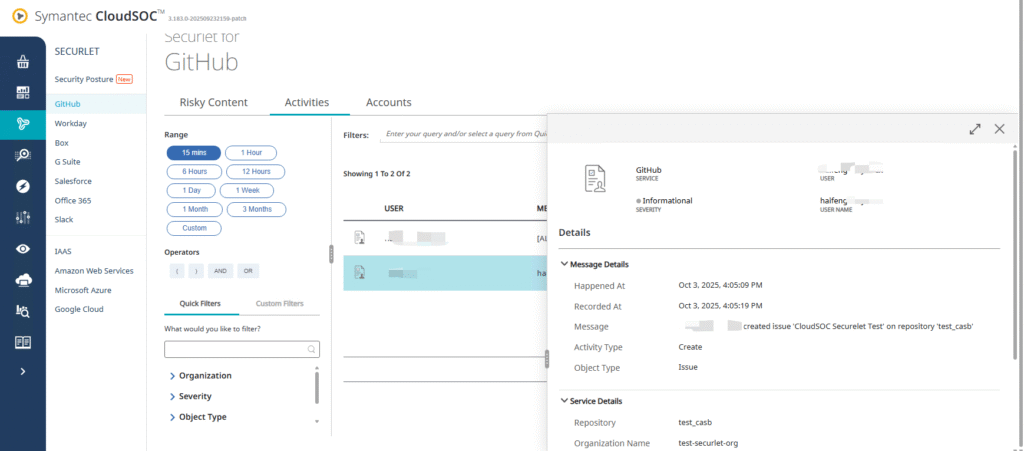
- You can also check same events via Investigate → Activities.
- If the policy conditions are met, an Alert will be generated.
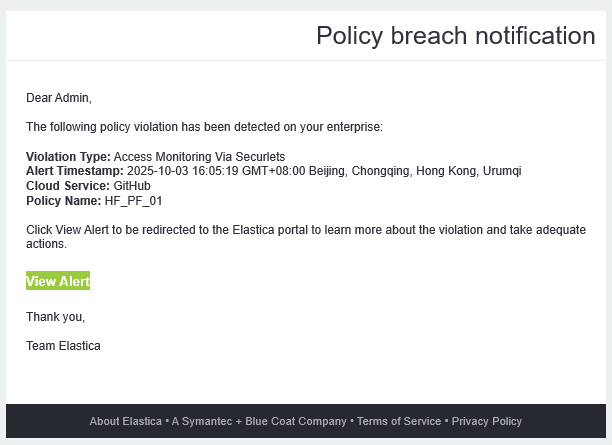
6. Verification
- The GitHub Securelet successfully captured the event.
- The configured policy (
HF_PF_01) matched the activity. - Notifications were sent according to the configured response template.
Recent Comments