Configuring GitHub Gatelet in Symantec CloudSOC
This guide describes how to configure the GitHub Gatelet in Symantec CloudSOC, activate control for GitHub traffic, and test the setup by creating a Pull Request to verify blocking behavior through a policy.
1. Prerequisites
Before starting, ensure you have:
- A CloudSOC administrator account
- A GitHub Organization with at least one repository
- The Gatelet feature enabled in your CloudSOC tenant (under CASB → Gatelets)
- Web traffic for GitHub routed through Cloud SWG
2. Activate the GitHub Gatelet
- Log in to the CloudSOC console.
- Navigate to STORE → Gatelets.
- In the app catalog, locate GitHub.
- Click Activate App.
- Once activated, the GitHub Gatelet icon will display a green check mark ✅, indicating that control is enabled.

🔸 No API authorization or GitHub account binding is required.
Gatelets analyze and enforce control based on network traffic observed via Cloud SWG.
3. Create a Policy to Block Pull Request Creation
- Go to Protect → Policies → Add Policy.
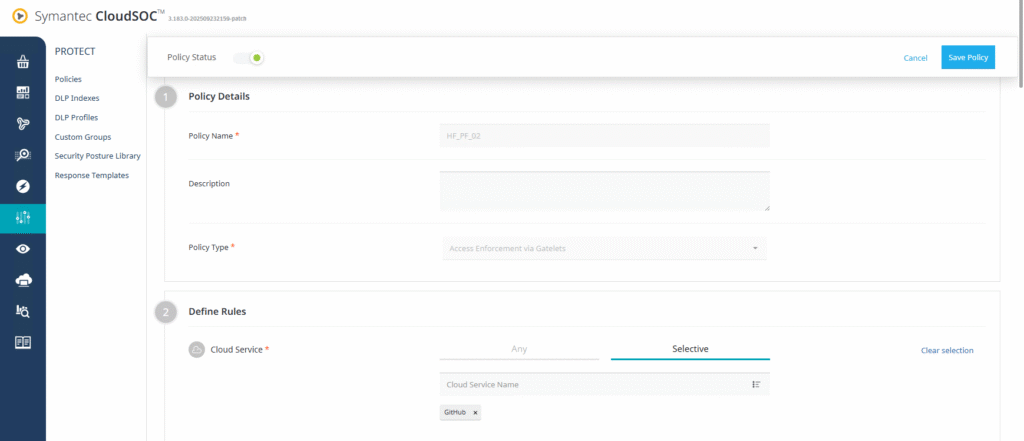
- Provide the policy details:
- Policy Name:
HF_PF_02 - Policy Type: Access Control via Gatelets
- Cloud Service: GitHub
- Policy Name:
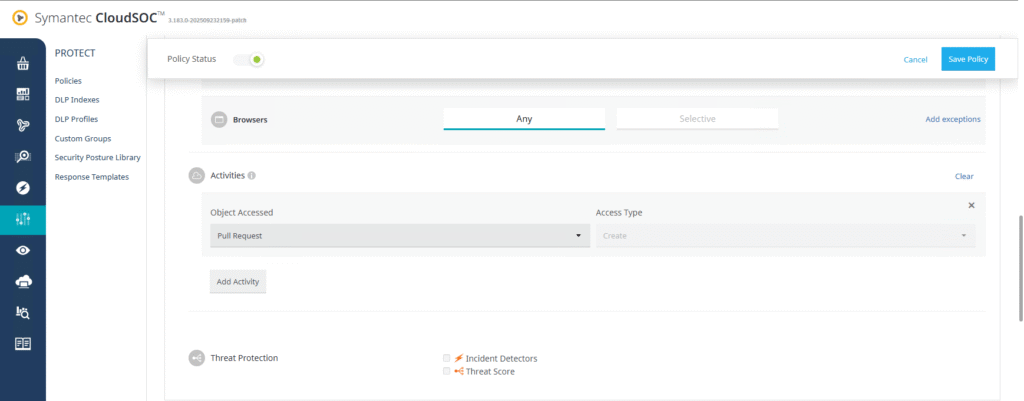
- Define the rule to block a specific activity:
- Object Accessed: Pull Request
- Access Type: Create
- Configure the enforcement action:
- Action: Block
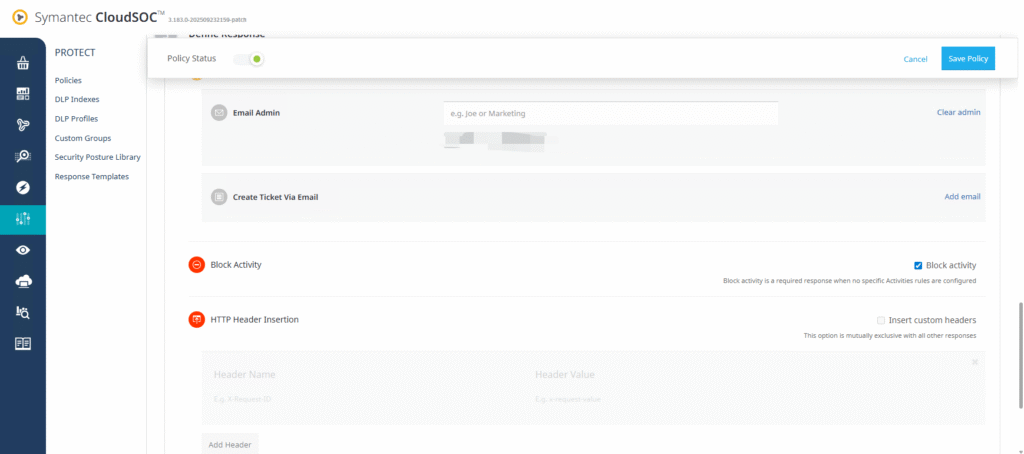
- Save and enable the policy.
Once active, this policy will prevent users from creating new Pull Requests while using GitHub through the CloudSOC-protected network.
4. Create unauthenticated User for Validation
To simulate an unauthenticated or non-domain user session:
- In the CloudSOC console, go to Users.
- Click Add User and create a unauthenticated account such as:
unauthenticated-user@lihaifeng.net - On Cloud SWG, configure a bypass rule for authentication so that this user’s traffic is passed without login.
5. Perform a Test Activity
To validate the GitHub Gatelet blocking policy:
- Log in to a workstation or browser session routed through Cloud SWG.
- Access GitHub (bypassed authentication).
- In a repository under your organization, attempt to create a new Pull Request:
- Title:
CloudSOC Gatelet Block Test - Description:
This Pull Request was created to test the GitHub Gatelet blocking policy.
- Title:
- When you submit, the action should be blocked by the configured policy.
- In CloudSOC, navigate to Protect → Policies → Alerts to confirm that the blocked attempt was recorded.
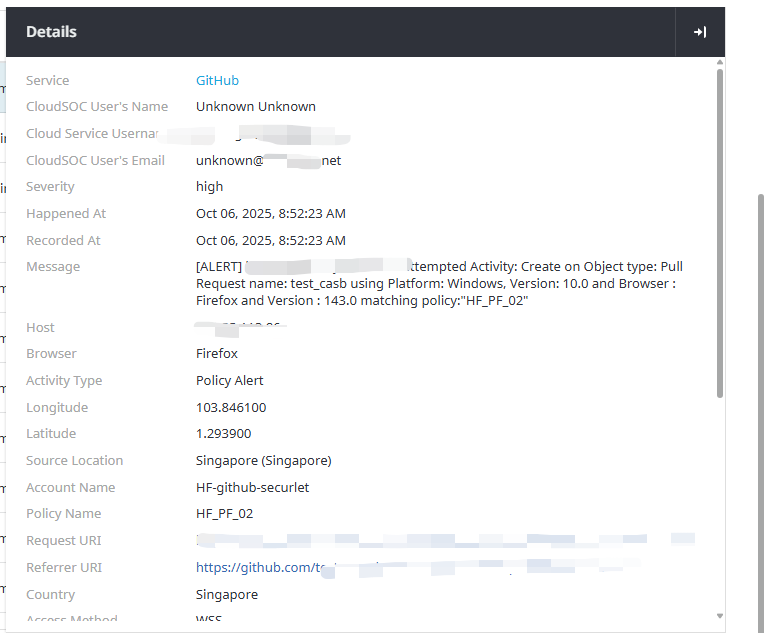
Note: When authentication is enabled, only users from the tenant’s primary or secondary domain are allowed.
6. Verification
If configured correctly:
- The GitHub Gatelet detected the Pull Request creation attempt.
- The policy (
HF_PF_02) blocked the action as expected. - The user session confirmed that Gatelet enforcement works even under bypassed authentication.
Recent Comments