Invalid Message-Authenticator? Try to calculate it!
Invalid Message-Authenticator is a common error in AAA authentication. The most likely cause is that the shared secret configured on the server and client do not match. If you are sure that there is no problem with the configuration, then we need to know whether the problem is on the server or the client.
Message-Authenticator is a HMAC-MD5 hash value, length is 18, as stated in the title we can calculate it. For the explanation of Message-Authenticator, we can refer to RFC 3579 , which will not be discussed here.
To calculate Message-Authenticator, we need the following two things.
1. Access-Request packet
2. Shared secret
Export and edit package
Access-Request can be filtered with radius.code == 1, and then right-click on Radius Protocol and select Export selected packet bytes. After saving it as a .bin file, we need to edit it.
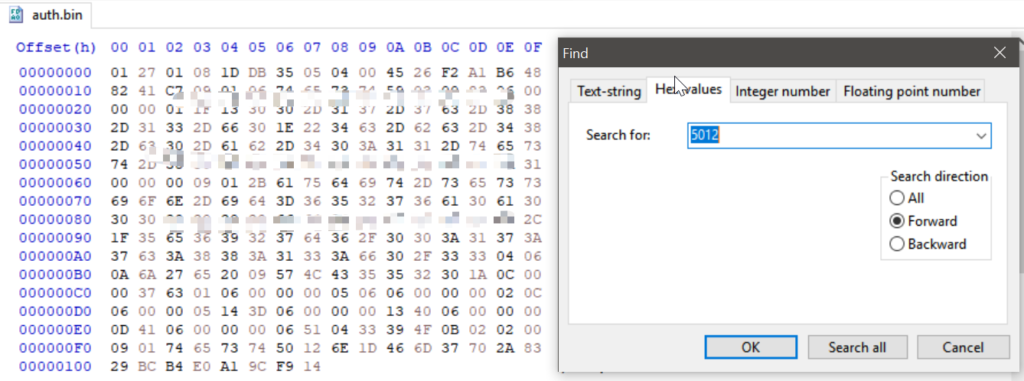
HxD is a free Hex Editor software, After installing HxD, we import the .bin file into HxD. Search and locate the value 5012, and fill all the values behind it with 0.
If you are using a Linux client, there are other options.
First we need to install the required packages (Ubuntu is used in the example).
root@yang-explorer-1:/tmp# apt install openssl root@yang-explorer-1:/tmp# apt install vim root@yang-explorer-1:/tmp# apt install xxd
Follow the steps below to edit the .bin file.
- Type <vim filename -b> to open the file
- Enter <:%!xxd> to switch to hexadecimal mode
- Enter <i> to enter edit mode
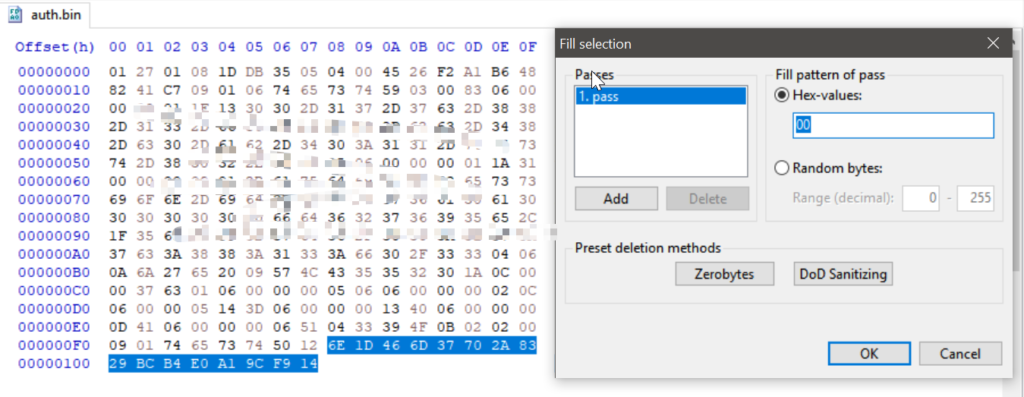
- Fill the values after 5012 with 0
- Press ESC to exit edit mode
- Enter <:%!xxd -r> to exit hexadecimal mode
- Enter <:wq> to save and exit
- Enter <xxd filename> to double check
Calculate the Message-Authenticator value
On the Linux client we can use the following command to calculate.
- cat filename | openssl dgst -md5 -hmac ‘shared secret’
Examples are as follows.
root@yang-explorer-1:/tmp# cat auth-edit.bin | openssl dgst -md5 -hmac 'cisco' (stdin)= 6e1d466d37702a8329bcb4e0a19cf914 root@yang-explorer-1:/tmp#
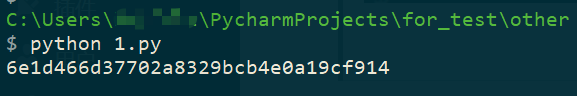
We can also use Python to calculate. The following is a Python 3 script.
import hmac
import hashlib
f = open('auth-edit.bin', 'rb')
try:
body = f.read()
finally:
f.close()
digest = hmac.new(bytes('cisco', 'ascii'), body, hashlib.md5)
d=digest.hexdigest()
print(d)
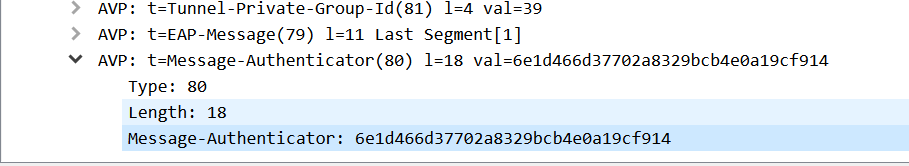
Compared with the Message-Authenticator value in the packet capture, we can see that the calculation result is matched – meaning that the value sent by the client is correct. If the AAA Server still shows “Invalid Message-Authenticator” at this time, then we have reason to suspect that the root cause of the problem is the AAA server, not the client.
Reference
RADIUS Invalid Authenticator and Message-Authenticator Troubleshoot Guide
Recent Comments